

Cyph + Tor = Privacy & Anonymity
Using Cyph secures your data and ensures that prying eyes won’t see the content of your data, but many inferences can still be made from metadata — like the fact that you’re connecting to an encrypted communication service at all, or even (with NSA-level access) potentially identifying that you’ve sent encrypted messages to certain users at certain times.
(We actually already partially mitigate this type of analysis by obfuscating the data sent over the network through various methods, such as padding each message with data of a random length, automatically sending random messages back and forth, and splitting traffic for each conversation all over the globe.)
Privacy
Can I determine the contents of your message?
Anonymity
Can I determine who you are and/or who you’re communicating with?
If you want to go a step further though and anonymize yourself while using Cyph, you just have to connect using our Tor hidden service: cyphdbyhiddenbhs.onion. It’s not hard; I’ll walk you through your options.
1. Setting up Tor
There are two primary ways to connect to Tor. You can set it up as a proxy and pass all or some of your traffic through it, or just download the Tor Browser Bundle. If you’re a non-technical user, the latter is far easier and faster to set up.
a. Tor Browser Bundle Setup
Since Tor Browser is the most common way most people access Tor, we’ll start there. It’s quick and easy to set up, but please note that Tor Browser does not provide you absolute protection, and must be used properly in order to ensure optimal safety when browsing. I highly recommend you take a look at the Tor list of warnings before actively using the browser.
Want Tor to really work? You need to change some of your habits, as some things won’t work exactly as you are used to.
Go ahead and download the latest Tor Browser Bundle by clicking the link below. It should automatically detect your operating system but if it gets it wrong, be sure to download the appropriate package.
Download Tor Browser
Before you install TBB, be sure to check verify the package signature. This will ensure that the software you install is exactly what it should be. If the signature doesn’t match, it’s possible someone has altered the package you downloaded with malware, or more plausibly that the data is corrupt somehow. Either way you don’t want to install it unless it matches.
Once you’ve verified the signature, run the package you downloaded. On Mac, drag the Tor Browser icon to the application folder; on Windows follow the setup wizard. It’s pretty foolproof. You’ll then have a Firefox fork installed which will connect to the Tor network every time you launch it. Please note that this does not route all your traffic through Tor, only traffic in the Tor Browser. If you’d like to route all your traffic, look into the more advanced setup below.
b. Tor Proxy Setup
If you’re looking for the advanced approach, chances are you won’t need my help getting set up, but here are some useful resources to point you in the right direction. Again, you don’t need to complete these steps if you’ve already downloaded the Tor Browser Bundle.
2. Connecting to Cyph
Once you’ve launched Tor Browser, all you really need to do is go to our Cyph onion address: https://cyphdbyhiddenbhs.onion. It’s pretty easy to remember if you break it up like this: Cyph’d by hidden BHS or Cyph’d by hidden Backbone Host Server.
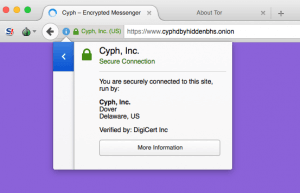
Be sure to check for the fancy green Extended Validation SSL bar reading “Cyph, Inc.” for extra peace of mind that you’re connected to the right service. (Fun fact: we were actually the the first company to be issued an EV SSL cert for an onion domain).
Tin Foil Hat: If you want to be extra careful, you can also connect through a SOCKS proxy or VPN; however this might further degrade performance.
Tin Foil Hat: If you want to be extra careful, you can also connect through a SOCKS proxy or VPN; however this might further degrade performance.
